According to CNBC, around $1.1B of cryptocurrency was stolen in just the first half of 2018. Cybercriminals try to exploit the weakest points in the crypto ecosystem and often find those points in cryptocurrency wallets.
A cryptocurrency wallet is typically a file that contains a user’s keys, including a private key - a piece of information that is needed to spend the user’s money. The wallets are password protected and naturally secure by themselves, but, via human error, are often rendered vulnerable: users make weak passwords, store them adjacent to their wallet files, or fail to use antivirus software. All these mistakes open the door for hackers to obtain wallet files with their corresponding passwords.
However, there is a solution that eliminates these threats altogether - hardware wallets. Hardware wallets have gained noticeable popularity in the last few years - they are used by consumers and businesses, including exchanges, to safely store cryptographical credential data outside of their computers. They are often used to facilitate cold storage - a means of storage that is not connected to the outside world to eliminate any risk of credential theft.
The principle behind hardware wallets
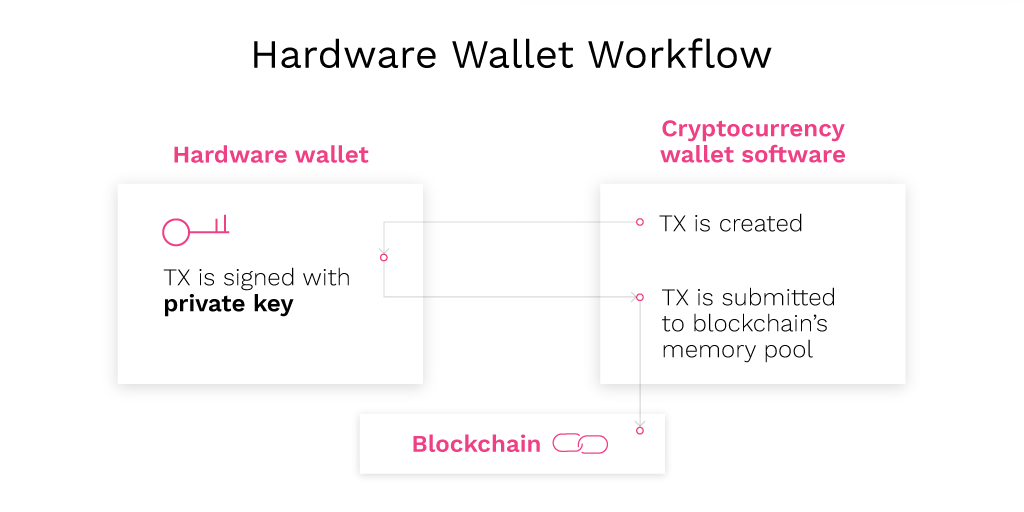
Hardware wallets are generally small devices that look like thumb drives or smartphones. Among the most popular are those produced by Ledger, Trezor, and KeepKey. The key principle of operation is that hardware wallets allow consumers to digitally sign a transaction without disclosing the private key to the computer from which a transaction is being sent.
In order to make that happen, the cryptographic keys are first loaded onto the hardware wallet. Then, whenever a transaction needs to be sent, it is first given to the hardware wallet, connected to a computer via cable or wireless connection. The hardware wallet uses the private key of the user to digitally sign a transaction and sends it back to the computer to be submitted to the blockchain. That way users are able to use their credentials without transferring them onto the computer, from which their transaction is being sent from.
Hardware wallets eliminate several threats at once:
- sensitive private data (the private key) is not transferred to the computer and therefore cannot be stolen by any malware on that computer;
- the wallet password is entered on the hardware wallet, rather than on the computer, eliminating the risk of being grabbed by keylogging malware. In addition, it cannot be brute-forced by malware, like a stolen wallet file;
- hardware wallets typically store credential data on a separate independent chip, making it physically impossible to hack it from the computer it is connected to.
Bytecoin early support for hardware wallets
The Bytecoin team announces early support for hardware wallets. This is a project that has been quite a long time in the making. The Bytecoin devs have made several important adjustments to bring this about.
First of all, the existing wallet structure was adapted to the widely used BIP-32 standard, employed by hierarchical deterministic wallets. Secondly, the devs have reserved position 204 (HEX number 0x800000cc) in BIP-44, a logical hierarchy for deterministic wallets.
It is important to point out that this document marks the start of early support for hardware wallets in Bytecoin Stagenet, not a Stable release. Users are free to download and test out the modified Bytecoin daemons for Linux. They have been placed in a dedicated branch in the main Bytecoin repository. A separate release has been created as well. A tutorial will be released later.
As always, your feedback on the performance or any bugs that you find is greatly appreciated on the GitHub repository or via support@bytecoin.org.
Support for hardware wallets marks an important security upgrade for Bytecoin. Via hard wallet support, both consumers and businesses would be provided with a more convenient authentication workflow. All feedback is greatly appreciated.
